Online Shopping Safety Tips
 Many holiday shoppers prefer to shop from the comforts of their home instead of brushing up on their karate skills in the Black Friday melee. While nothing says comfort like H-O-M-E, cyber predators are working overtime to make sure they can get a piece of someone’s pie. Since we’re all about online safety around these parts, 24HourSupport wants to send you off shopping in happy-style with these online safety tips.
Many holiday shoppers prefer to shop from the comforts of their home instead of brushing up on their karate skills in the Black Friday melee. While nothing says comfort like H-O-M-E, cyber predators are working overtime to make sure they can get a piece of someone’s pie. Since we’re all about online safety around these parts, 24HourSupport wants to send you off shopping in happy-style with these online safety tips.
Of course, before you begin shopping, you want to ensure that your computer is protected with updated security software including anti-virus and anti-malware protection. Your operating system and web browsers should also include the latest updates as well.
1. Shop Trusted Websites
Many fake websites spring up during the holidays just to dupe unsuspecting shoppers into thinking they are getting deals when in fact, the website owners are making off with personal information looking for a pay day. Even though online retailers tend to slash prices for holiday shopping, the old saying “if a deal seems too good to be true, it probably is” will certainly continue to ring true. Bottom line – stick with who you know.
2. Safeguard Your Passwords
When shopping online, many websites allow you to register and provide a password so that you may store your personal information for convenience. If you opt to do this, ensure that you create secure passwords, and if you must store them, store them in a secure place away from prying eyes as it can become difficult to remember various passwords.
3. Make Sure Your Purchase is Secure
Most online retailers have implemented secure transactions to provide shoppers with peace of mind in knowing that their purchases are protected. When making a secure purchase online, always look in your web browser’s address bar for “https://” to indicate that you are using a secure transaction.
4. Use Credit Cards If Possible
While debit cards have provided many shoppers the convenience of not racking up credit card debt while shopping, these types of cards are most often linked to a bank account that can be drained if intercepted into the wrong hands. Credit card companies have policies in place for fraud prevention, so although you may not want to use credit, think about the cash you could stand to lose if using debit.
Is Your Amazon Email a Fake?
Christmas is nearing, and many online shoppers are anxiously awaiting informational emails from purchases that have been made. Did my order go through? Will my shipment make it in time? Did my shipment get lost in transit? Having to worry about these types of issues makes them leap for joy when they see an email in their inbox about their order.
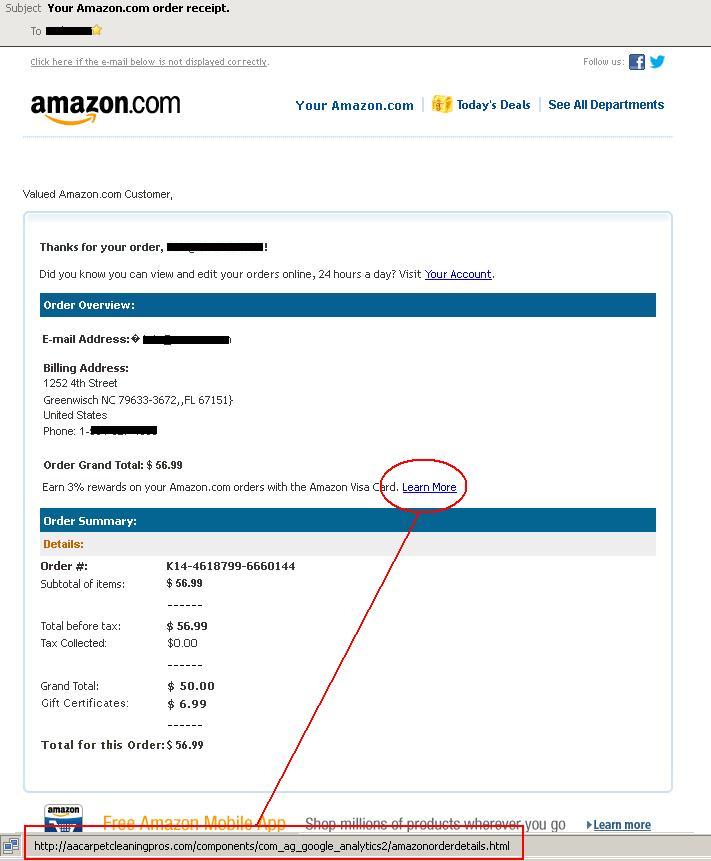
Amazon is the latest online retailer to feel the burn of phishing scams as users are beginning to receive emails similar to the one below that appear to be from Amazon but are in fact phishing scams. As with most other fraudulent emails, it may be difficult to tell that the email isn’t real at first glance because scammers are getting better at making their emails look more like the actual emails that are sent from Amazon. Spotting the fakes can be a bit tricky, but you can use these helpful tips to keep up with the latest string of Amazon phishing emails:
1. If the email contains an unsolicited attachment, it did not come from Amazon.
2. Avoid clicking on links in a suspicious email. In the below example, the “Learn More” link redirects to a website that is not affiliated with Amazon, which is a clear indication of a scam.
3. Amazon will never request personal information such as passwords or bank information via email. This type of information is only collected on the Amazon website.
4. Look for grammatical errors and typos in the email. Legitimate Amazon emails are not likely to contain these types of errors.
If you need to report a fraudulent email to Amazon, you may use the contact form that is available here to alert them.
Remember to always keep updated anti-virus and anti-malware software on your computer and scan it regularly to protect yourself.
Getting Started: Windows 8 Quick Tips
 How many of you opened a shiny, new Windows 8 laptop this past Christmas? Was it what you were expecting or were you totally shocked? Microsoft did a vast makeover on its Windows operating system with the inception of Windows 8, and you may not have known where to begin or even if you wanted to begin! If you’re here, we’re assuming that you decided to take a plunge into the unknown and get to know your Windows 8 computer. Since we thought you could use a helping hand to get you through the new year, here are a few quick tips to help you get started:
How many of you opened a shiny, new Windows 8 laptop this past Christmas? Was it what you were expecting or were you totally shocked? Microsoft did a vast makeover on its Windows operating system with the inception of Windows 8, and you may not have known where to begin or even if you wanted to begin! If you’re here, we’re assuming that you decided to take a plunge into the unknown and get to know your Windows 8 computer. Since we thought you could use a helping hand to get you through the new year, here are a few quick tips to help you get started:
- How do I use the Charms in Windows 8?
- There’s no start button. How do I use the Start Screen?
- How can I get back to my desktop?
- How do I access the Control Panel in Windows 8?
- How do I search for files in Windows 8?
- How can I access Help and Support in Windows 8?
- How do I shut down my Windows 8 computer?
The Forgotten One: Smartphone Mobile Security
 While a smartphone is a mobile device, it is still essentially connecting to a network whether it be a cellular provider or some form of Wi-fi connectivity. Just like computers, smartphones need to have some type of security software contained to ensure that you are protecting your personal data. You don’t want to be at the counter purchasing food and your debit card is declined because someone has wiped out your bank account. To help you stay smart on your phone, below you’ll find resources to get you started on finding the mobile security that is right for you.
While a smartphone is a mobile device, it is still essentially connecting to a network whether it be a cellular provider or some form of Wi-fi connectivity. Just like computers, smartphones need to have some type of security software contained to ensure that you are protecting your personal data. You don’t want to be at the counter purchasing food and your debit card is declined because someone has wiped out your bank account. To help you stay smart on your phone, below you’ll find resources to get you started on finding the mobile security that is right for you.
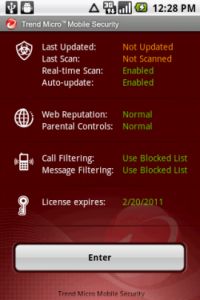
Trend Micro Mobile Security: Named as one of PC World’s Best Products in 2011, Trend Micro’s personal edition of its mobile security software is exclusive to Android devices. The malware and virus scanner are helpful in identifying attachments in emails that may compromise your data as well as nasty viruses that may be lurking in apps that you download. Privacy is essential on smartphones and Trend Micro has beefed up its privacy protection to keep your your personal information in a safe place – on your phone.
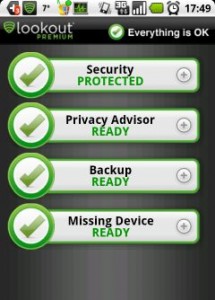
Lookout Mobile Security: This is probably one of the most popular mobile security suites and can be found in Android and iOS app stores in the free and premium versions. You can expect to have regular scans for malware and viruses, protection when clicking malicious URLs, find my phone features, and more.
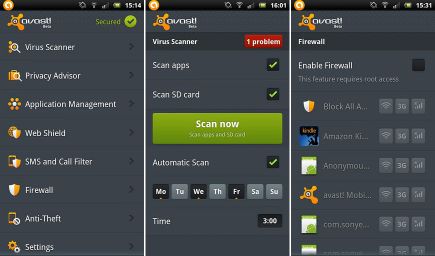
Avast Free Mobile Security: Another Android exclusive app, Avast packs a powerful punch with the features contained in this freebie. With malware/virus scanning to phone locator features, SMS blocking, and even a network meter that lets you know when you’re reaching monthly data limits, you can have peace of mind knowing that your smartphone is in good hands. Literally.
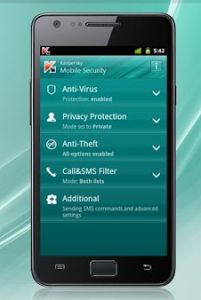
Kapersky Mobile Security: Scaling down it’s protection capabilities to the mobile form, Kapersky Mobile Security can be downloaded to your Android phone to ward of malware, trojans, and viruses. It can also be used to erase date from your phone in the event that you are unable to locate it with it’s phone location features. Another of its popular features is the ability to ward off unwanted phone calls and SMS text messages. Who wouldn’t want that?
24HourSupport Chat to the Rescue
 It’s 2am, and you’re trying to send an email message, but your message keeps getting rejected. For some reason, you can’t remember your email settings and need them NOW. What do you do?
It’s 2am, and you’re trying to send an email message, but your message keeps getting rejected. For some reason, you can’t remember your email settings and need them NOW. What do you do?
Of course you can always call technical support and get the information, or you can connect instantly with one of our technical support representatives on our 24HourSupport Live Chat.
How does this work, you say?
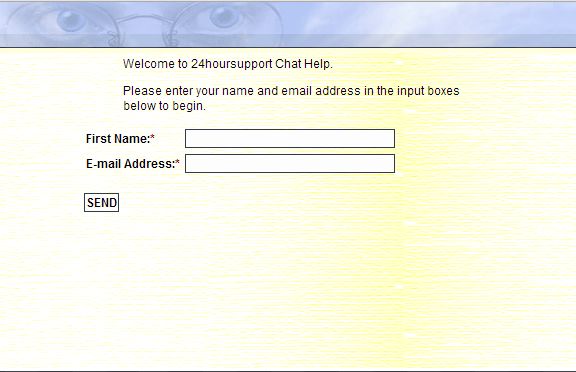
If you’re on your broadband provider’s website, you can click the Live Chat button to be connected, or you can click the Live Chat button on the Contact Us page that is available on 24HourSupport.com. You’ll need to enter your name and email address to get started. Once your request is sent, you will be connected with the first available technical support representative and be on your way to getting your problem solved.
Secure Password Tips
 If you’re like most users, you probably have several online accounts that require passwords. And, if you’re like most users, you probably use something easy to remember or maybe even use the same password for multiple accounts. With hacking on the rise and users’ accounts being compromised on a daily basis, it’s important to create secure passwords to keep your personal information safe.
If you’re like most users, you probably have several online accounts that require passwords. And, if you’re like most users, you probably use something easy to remember or maybe even use the same password for multiple accounts. With hacking on the rise and users’ accounts being compromised on a daily basis, it’s important to create secure passwords to keep your personal information safe.
You can get started with these general secure password tips from 24HourSupport because your accounts are only as safe as your passwords.
- Your password should contain between 6 and 16 characters.
- Passwords should begin with a letter or number and should contain at least one letter and a number or one of the following special characters: _ – . @ %.
- Common sequences such as “abcd” or “1234″ should be avoided.
- Passwords are case sensitive, so mixing upper and lower case letters will make your password more secure.
- Your username and password should never be the same.
- When using a single device (ex: computer, tablet, smart phone) to access multiple accounts that require logging in, it is best to use a different username/password combinations for each account.
- Check your password with an online secure password checker to get an idea of how weak or strong the password may be.
Trojan Yontoo on the Prowl for Mac OS X
 The myth of adware and malware not being directed at Mac computers is being further debunked as the latest threat to OS X comes in the form of a trojan injecting ads into popular web browsers. Users of Mozilla Firefox, Google Chrome, and Apple’s Safari web browser should be on the look-out for the Trojan.Yontoo.1 adware that is inserts itself into the browsers of infected systems.
The myth of adware and malware not being directed at Mac computers is being further debunked as the latest threat to OS X comes in the form of a trojan injecting ads into popular web browsers. Users of Mozilla Firefox, Google Chrome, and Apple’s Safari web browser should be on the look-out for the Trojan.Yontoo.1 adware that is inserts itself into the browsers of infected systems.
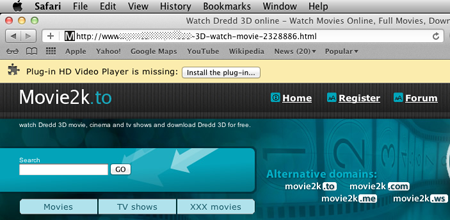
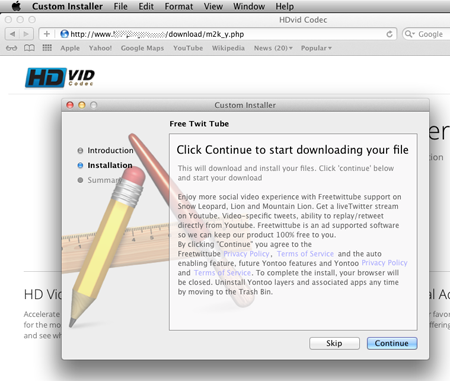
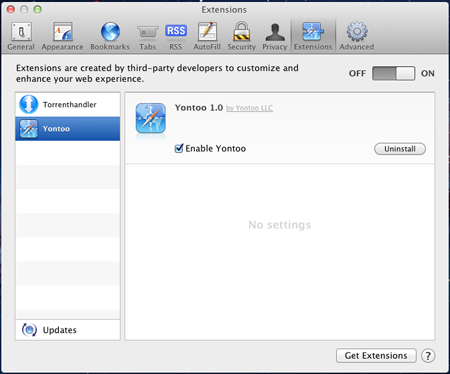
Although there are various methods for Yontoo to entrap users, it primarily lures its victims in to watch movie trailers requiring a download of a plug-in to view the full trailer. Of course, if users are really interested in the movie, most will attempt to install the plug-in which in turn actually installs Yontoo onto their computers. Once installed, Yontoo begins tracking the information from the websites that are visited to a remote server and information from the server is then returned that embeds the adware into the pages that the user has browsed to.
Those affected should install the latest OS X updates as Apple has included the latest definitions for XProtect to remove Yontoo.
See Yontoo in actions in the screenshots below.
Linksys Routers Seeing Attacks from The Moon Malware
 Everyone wants to enjoy the convenience of having a wireless home or office network, but malware developments continue to threaten the security and create unauthorized access if the appropriate security measures are not taken. Linksys recently identified a strain of malware that is being called “The Moon” that exploits the firmware in certain older model Linksys devices, primarily the E-series routers and older models of the Wireless-N access points and routers.
Everyone wants to enjoy the convenience of having a wireless home or office network, but malware developments continue to threaten the security and create unauthorized access if the appropriate security measures are not taken. Linksys recently identified a strain of malware that is being called “The Moon” that exploits the firmware in certain older model Linksys devices, primarily the E-series routers and older models of the Wireless-N access points and routers.
Login credentials are at stake because “The Moon” bypasses the available login information and generally infects the device once it has gained access to it. The malware then begins to send out large amounts of unsolicited outbound requests over the Internet increasing data usage. One of the preliminary symptoms that you’ll notice is that your Internet connection may appear to slow down. Linksys has provided a description of what is resulting from “The Moon” malware and offered a work-around patch here until they are able to permanently resolve the issue.

No More Updates for Mac OS X Snow Leopard
 Most Apple computer users don’t have security vulnerabilities high on their list because historically, Mac computers have been relatively secure. Users of the popular OS X 10.6 Snow Leopard version need to start thinking about other alternatives if they expect their online activities to remain safe because Apple seemingly is no longer offering support for Snow Leopard.
Most Apple computer users don’t have security vulnerabilities high on their list because historically, Mac computers have been relatively secure. Users of the popular OS X 10.6 Snow Leopard version need to start thinking about other alternatives if they expect their online activities to remain safe because Apple seemingly is no longer offering support for Snow Leopard.
According to this report from Computer World, Apple updated it’s last three versions of the OS X software, Mac OS X 10.9 Mavericks, Mac OS X 10.8 Mountain Lion, and Mac OS X 10.7 Lion, on Tuesday, but OS X 10.6 was left out in the cold.
What does this mean for Snow Leopard users?
Since there hasn’t been an update for Snow Leopard since September 2013, it would be safe to say that OS X 10.6 users need to consider updating their version of the OS. Before you begin updating, you have to ensure that your Mac computer running Snow Leopard has hardware that is compatible with OS X Mavericks. You can find Mavericks’ system requirements here. Happy updating!
Upgrade from Mac OS X 10.6 Snow Leopard to OS X Mavericks
If you are running Mac OS X 10.6.8 or later:
- Find out if your Mac can run OS X Mavericks.
- Back up your Mac.
- Get OS X Mavericks from the Mac App Store.
- Double-click Install OS X Mavericks to begin installation.
If you are running Mac OS X 10.6.7 or earlier:
- Find out if your Mac can run OS X Mavericks.
- Back up your Mac.
- Run Software Update to upgrade to the latest version of Snow Leopard (v10.6.8).
- Get OS X Mavericks from the Mac App Store.
- Double-click Install OS X Mavericks to begin installation.
Getting Started with WiFi on Roku
 Like to stream movies and TV shows? Then more than likely, you’ve encountered a streaming media player at some point. While they can be connected to a wired home or office network, enjoying the convenience of Wifi just doesn’t seem to evade us. For those of you that have settled on the Roku streaming media player, here are a few tips to get you started and connected to Wifi.
Like to stream movies and TV shows? Then more than likely, you’ve encountered a streaming media player at some point. While they can be connected to a wired home or office network, enjoying the convenience of Wifi just doesn’t seem to evade us. For those of you that have settled on the Roku streaming media player, here are a few tips to get you started and connected to Wifi.
Getting Started
To begin, you’ll need your Roku device and accessories, a Wifi connection, and an HDMI cable if you’ll be connecting your device to a high-definition TV (HDTV). Otherwise, have your component/composite cables handy for a standard definition TV. Connect the cables of your choice from your Roku media player to the back of your TV.
Connect to Wifi
- Step 1: Power on your Roku device
- Step 2: From the home screen select Settings
- Step 3: Select Network
- Step 4: Select Wireless
- Step 5: Your Roku device will now scan for all wireless networks in range
- Step 6: Select your network name from the list and choose Connect & enter your wireless password for your WiFi
- Step 7: Your wireless information should come up on the screen once the connection is successful.
Enjoy the Stream
One you’ve connected your Roku device to your Wifi connection, the media player will reboot and update to the latest software for your particular device. You’ll then proceed through the set up screen and be quickly on your way to enjoying the channels that you select. Happy streaming!